Intro : Hello Hackers! Welcome to new CTF writeup on HackTheBox machine Office. Here you will find Common Joomla CVE (Same in HTB Devvortex Machine), Hash Cracking & get User Access. So let;’s Jump into the Hack.
Nmap Scan
As usual I start with a Basic Nmap Scan and I found many Ports are Open as it is a Windows Machine. From here I found Port : 80, 139, 88, seems Interesting.
Firstly I add office.htb in my Host File.
Web Exploitation
So I start the Web Enumeration. And I saw it is running on Joomla CMS.
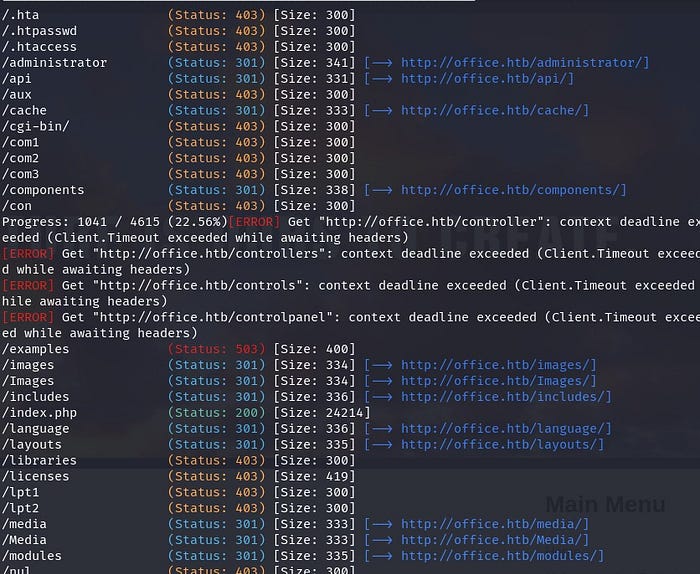
I start a Basic Gobuster Scan to find any Hidden Directory.
I notice there is also a Admin Panel of Joomla.
So I start enumerate the Version of this Joomla CMS and I found it. The Path is → /administrator/manifests/files/joomla.xml
And I found It is Vulnerable for Unauthenticated information disclosure.
Using to the POC I collect the Valuable Endpoints to get the Password.
I try to Login with this Creds in the Admin Panel but it failed. It is wired soo I start my Enumeration Again. I saw Kerberos Protocol is Open so I can use Kerbrute to Enumerate Domain Users.
Note : Here I use Seclists
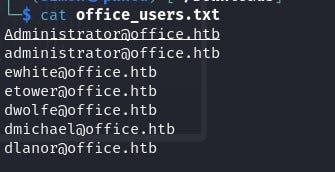
And I found some Valid User’s Account.
So here I try which User can use the Previous Leaked Password for login as SMB using Crackmapexec.
Here I found the valid user : dwolfe. Now I use impacket-smbclient to access SMB Shares.
Here I found a share named : SOC Analysis. I access that Share and I found a pcap File. I download that in my Kali VM.
After opening that pcap file with Wireshark I filter the Kerberos Protocol.
Here I found an Encrypted Password hash. We can crack it using Hashcat. Follow the Blog below.
I already cracked it.
After that I try to login with Administrator and the cracked Pass. This time I logged into the Dashboard.
Here we can try to Upload a PHP shell to get Shell Access in the Box. I use Powny Shell to do that. For this you have to go to System > Template > index.php. Now you have to Replace the Existing Content with that PHP Shell and save it.
Now if you load the Main Page you will get Shell access from your Browser.
But we get a Shell as a web_account User. Later I transfer this shell in my Terminal with netcat.
Then I upload a Msfvenom Reverse Shell in the target VM to get shell access from Metasploit.
Privilege Escalation → tstark :
First I listed the Available Users in the Machine.
From here I found tstark User Interesting because in the Web Page most of the Posts related on Iron Man 🙂
So here I run a Metasploit Module to run command as tstark User.
Note : You can also use RunasCs to do that.
Steps : 1> Open Powershell
2> Import-Module ./<ps1_file>
3> Invoke-RunasCs -Username <user> -Password <pass> -Command <cmd>
Here in the Desktop I got the User Flag.
That’s it. I am now working to get Root Access. It will be published soon.
THANKS FOR RAEDING!
If you like it don’t forget to Like it and Follow me for more Articles.
Happy Hacking~ HackerHQ
FAQs
- What is HackTheBox (HTB)?
HTB is an online platform for cybersecurity
challenges.
- How can I access the Office HTB challenge?
You need an
active HTB subscription and VPN access.
- Is prior hacking experience required for Office HTB?
No, but
basic knowledge is helpful.
- Are there prerequisites for attempting Office HTB?
Familiarity
with networking and Linux basics is useful.
- Can I collaborate with others on Office HTB?
Collaboration
is allowed via HTB forums.
- Is it legal to attempt challenges on HTB?
Yes,
challenges are legal and educational.
- How long does Office HTB typically take?
Completion
time varies based on skills.
- Are there rewards for completing Office HTB?
No monetary
rewards, but valuable experience.
- What to do if stuck during Office HTB?
Seek help
from forums or online resources.
- Can I share my Office HTB writeup?
Yes,
encouraged for knowledge sharing.